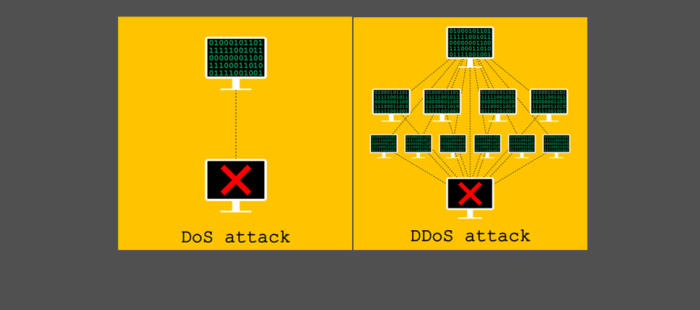
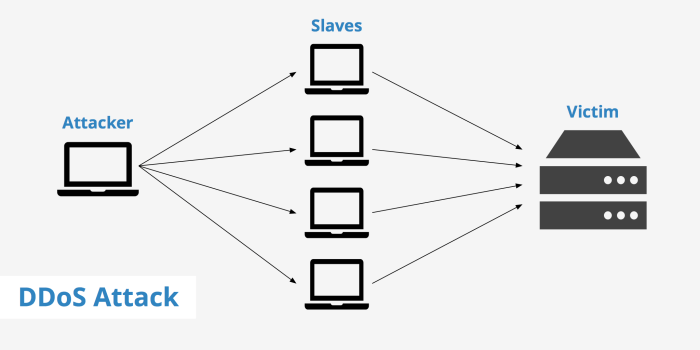
Watch what happens during a DDoS attack: Imagine a digital tsunami crashing against your website, overwhelming its defenses and leaving a trail of frustrated users and lost revenue in its wake. This isn’t some sci-fi movie; it’s the harsh reality of a Distributed Denial-of-Service attack, a cyber assault that can cripple even the most robust online platforms. We’ll dissect the mechanics, observable effects, and strategies for surviving this digital deluge.
From understanding the different types of DDoS attacks – volumetric, protocol, and application – to recognizing the telltale signs of an attack, we’ll equip you with the knowledge to navigate this complex landscape. We’ll delve into the network behavior during a DDoS, examining traffic patterns and key metrics to identify the threat. And, importantly, we’ll cover mitigation and response strategies, from deploying firewalls and intrusion detection systems to implementing rate limiting and traffic filtering.
Observable Effects During a DDoS Attack
A Distributed Denial-of-Service (DDoS) attack can manifest in a variety of ways, significantly impacting a website’s availability and user experience. Understanding these observable effects is crucial for both website owners and users to identify and respond to such attacks effectively. The symptoms can range from minor slowdowns to complete website outages, depending on the scale and sophistication of the attack.
The core issue during a DDoS attack is the overwhelming flood of traffic directed at the target server or network. This flood renders the system incapable of responding to legitimate requests from users, effectively bringing the service down or making it extremely difficult to access. The impact can be felt across different layers of the online experience, affecting everything from website loading times to overall network connectivity.
Website Performance Degradation
During a DDoS attack, website performance suffers dramatically. Simple actions like loading a webpage can become excruciatingly slow, or completely impossible. Imagine trying to access your favorite online store during a major sale – that’s the kind of slowdown, but on a much larger and more disruptive scale. Pages might take minutes to load, or users might encounter error messages indicating server overload or unavailability. Interactive elements, like search bars or shopping carts, might become unresponsive, further hindering the user experience. In extreme cases, the entire website might become completely inaccessible, displaying a blank page or an error message. This can severely impact a business’s revenue and reputation. For example, a major e-commerce site experiencing a DDoS attack during peak shopping hours could lose millions in potential sales.
Network Infrastructure and Connectivity Impact
The effects of a DDoS attack aren’t limited to the website itself; they ripple outwards to impact the entire network infrastructure. The sheer volume of malicious traffic can saturate network bandwidth, causing significant slowdowns or outages for other services sharing the same infrastructure. This can affect not only the targeted website but also other websites or services hosted on the same server or network. Imagine a large building with multiple businesses. If one business is under attack, the shared internet connection for the entire building might be severely affected, impacting all businesses within. This cascading effect can cause widespread disruption, affecting a broader range of users and services beyond the initial target. Furthermore, the attack can overwhelm routers and firewalls, leading to network instability and connectivity issues.
Typical User-Reported Issues
The experience of a user under DDoS attack is frustrating and often confusing. Here are some common complaints:
Users facing a DDoS attack frequently report experiencing several issues. The sheer volume of problems makes it difficult for users to understand the root cause, further exacerbating the frustration.
- Extremely slow loading times for websites
- Inability to access websites entirely – encountering “server not found” or similar error messages
- Intermittent connectivity issues, with websites loading sporadically or dropping connection frequently
- Unresponsive website elements, such as search bars, forms, or shopping carts
- General network instability, affecting other online services besides the targeted website
Network Behavior Under DDoS
A Distributed Denial-of-Service (DDoS) attack fundamentally alters a network’s behavior, overwhelming its resources and disrupting normal operations. Understanding these changes is crucial for effective mitigation and incident response. The key lies in recognizing the stark differences between legitimate high traffic and malicious flooding.
Network traffic patterns during a DDoS attack exhibit significant deviations from normal operations. The most noticeable change is a dramatic surge in network traffic volume, often exceeding the network’s capacity. This flood of packets, originating from numerous compromised sources, targets specific network services or resources, effectively choking them.
Key Metrics Indicating a DDoS Attack
Several key metrics provide strong indicators of an ongoing DDoS attack. Consistent monitoring of these metrics is essential for early detection and response. High values, especially sudden spikes, warrant immediate investigation.
- Bandwidth Consumption: A rapid and significant increase in bandwidth usage, far exceeding typical peak levels, is a primary indicator. For example, a website normally handling 1Gbps might suddenly see a 10Gbps influx during an attack.
- Packet Loss: As the network becomes overwhelmed, packet loss increases dramatically. This means that a substantial portion of the data packets fail to reach their destination. High packet loss often accompanies bandwidth saturation.
- Latency: The time it takes for data packets to travel across the network increases significantly. High latency translates to slow response times for users and applications.
- CPU and Memory Utilization: Network devices, such as routers and firewalls, experience a surge in CPU and memory utilization as they struggle to process the massive influx of malicious traffic. This can lead to system instability and crashes.
Hypothetical Network Diagram Illustrating DDoS Traffic Flow
Imagine a simple e-commerce website (Target) protected by a load balancer (LB) and a firewall (FW), all connected to the internet (Internet). The attack originates from numerous compromised devices (Botnet) across the globe.
The diagram would show a multitude of arrows originating from various points on the “Internet” section, all converging on the load balancer and the firewall. These arrows represent the massive influx of malicious traffic from the botnet. The load balancer, overwhelmed by the sheer volume, struggles to distribute the traffic, resulting in some packets being dropped. The firewall, also under immense pressure, attempts to filter the malicious traffic, but a significant portion gets through, reaching the target servers. The target servers show a substantial increase in resource usage (CPU and memory) depicted by shaded areas within their boxes. The legitimate user traffic (represented by fewer, thinner arrows) is severely impacted by the DDoS flood, leading to slowdowns and service disruptions.
Comparison of Network Behavior During Legitimate High-Traffic and DDoS Attacks
While both legitimate high-traffic events and DDoS attacks cause increased network traffic, several key differences exist. Legitimate traffic, such as during a popular sale event, is characterized by a gradual increase in traffic, originating from diverse and legitimate sources. Network resources are strained, but the system generally remains stable. Packet loss and latency are relatively low.
Conversely, DDoS attacks feature an abrupt and massive surge in traffic from a concentrated number of compromised sources. This results in rapid resource exhaustion, significant packet loss, high latency, and often system instability or crashes. The traffic pattern is significantly different; legitimate high traffic exhibits a natural ebb and flow, while DDoS traffic is typically a sustained, relentless flood. Detecting this difference relies on identifying unusual traffic patterns, volume spikes, and the source IP addresses of the incoming traffic. A sudden influx from numerous geographically dispersed IP addresses strongly suggests a DDoS attack.
Mitigation and Response Strategies
Facing a DDoS attack is like battling a swarm of angry bees – overwhelming and potentially devastating. A swift and well-coordinated response is crucial to minimize damage and restore service. Effective mitigation involves a multi-layered approach, combining proactive security measures with reactive incident handling.
Responding to a DDoS Attack: A Step-by-Step Guide
A DDoS attack requires immediate action. Delaying the response can significantly increase the damage. This step-by-step guide Artikels the critical actions to take.
- Detect the Attack: Utilize monitoring tools to identify unusual network traffic patterns indicative of a DDoS attack. This might include a sudden spike in traffic volume, requests from unusual sources, or a saturation of specific network resources.
- Analyze the Attack: Determine the type of DDoS attack (e.g., volumetric, protocol, application layer), its source(s), and the targeted resources. This analysis informs the mitigation strategy.
- Implement Mitigation Strategies: Employ various security technologies (detailed below) to filter malicious traffic and protect vulnerable resources. This might involve activating rate limiting, using a CDN, or employing blackholing techniques.
- Engage Your DDoS Mitigation Provider (if applicable): If you have a DDoS mitigation service, immediately contact them to leverage their expertise and resources. Many providers offer 24/7 support and advanced mitigation capabilities.
- Monitor and Adapt: Continuously monitor the network traffic to assess the effectiveness of the mitigation strategies. Adjust your approach as needed, potentially scaling up mitigation efforts if the attack persists or intensifies.
- Post-Incident Analysis: After the attack subsides, conduct a thorough post-incident analysis to identify vulnerabilities exploited by the attackers. This analysis should inform improvements to your security posture.
The Role of Security Technologies in DDoS Mitigation
Several security technologies play a crucial role in mitigating DDoS attacks. Their effectiveness is often maximized when used in combination.
- Firewalls: Act as the first line of defense, filtering traffic based on pre-defined rules. Advanced firewalls can identify and block malicious traffic patterns associated with DDoS attacks.
- Intrusion Detection/Prevention Systems (IDS/IPS): Monitor network traffic for suspicious activity, including DDoS attack signatures. IPS systems can actively block malicious traffic identified by the IDS.
- Content Delivery Networks (CDNs): Distribute website traffic across multiple servers geographically dispersed. This distributes the attack load and prevents a single server from being overwhelmed.
Rate Limiting and Traffic Filtering
These techniques are fundamental to DDoS mitigation. They help control the flow of incoming traffic, preventing malicious traffic from overwhelming network resources.
Rate limiting restricts the number of requests from a single IP address or network within a specific time frame. For example, limiting the number of login attempts per minute from a single IP can prevent brute-force attacks. Traffic filtering involves inspecting incoming traffic and blocking packets that match specific criteria, such as known malicious IP addresses or suspicious patterns.
DDoS Attack Response Decision-Making Flowchart
A flowchart visualizing the decision-making process would show a series of interconnected boxes. The first box would be “Detect DDoS Attack?”. If yes, the next box would be “Analyze Attack Type and Source?”. This would lead to a series of decision points, such as “Is it a volumetric attack?”, “Is it a protocol attack?”, and so on. Each decision point would branch to different mitigation strategies, like “Implement rate limiting”, “Engage DDoS mitigation provider”, “Utilize CDN”, etc. Finally, a box indicating “Monitor and Adapt” would signify continuous assessment and adjustment of the mitigation strategy.
Analyzing Attack Traffic: Watch What Happens During A Ddos Attack
Unraveling the mystery of a DDoS attack isn’t about staring blankly at a wall of network data; it’s about detective work. Understanding the attack traffic is crucial to effective mitigation and prevention. This involves meticulously examining network logs, identifying patterns, and pinpointing the source and type of attack. Think of it as forensic analysis for your network.
Analyzing network logs and identifying malicious traffic patterns during a DDoS attack requires a systematic approach. This process involves examining various data points to detect anomalies and understand the attack’s characteristics. By correlating different data sources, security professionals can piece together the attack’s timeline, scope, and origin. It’s like assembling a puzzle, where each piece of data reveals more about the bigger picture.
Network Log Analysis Techniques
Effective analysis relies on understanding the structure and content of various network logs. This includes examining firewall logs for unusual traffic spikes, intrusion detection system (IDS) alerts for suspicious activities, and router logs for bandwidth consumption patterns. Each log type provides a unique perspective, offering a more complete picture when analyzed together. For example, analyzing firewall logs might reveal a massive increase in connection attempts from a specific IP address range, while IDS alerts might highlight the use of specific attack vectors, like SYN floods or UDP floods.
Common Tools for Attack Traffic Analysis
Several tools assist in analyzing network traffic during a DDoS attack. These tools range from open-source command-line utilities like tcpdump and Wireshark, which allow for deep packet inspection, to sophisticated Security Information and Event Management (SIEM) systems that correlate data from multiple sources. Commercial network monitoring tools also offer advanced features such as real-time visualization of traffic patterns and automated anomaly detection. Choosing the right tool depends on the complexity of the network and the level of detail required for analysis. For instance, Wireshark’s packet-by-packet analysis is invaluable for identifying subtle attack signatures, while a SIEM system can provide a broader overview of the attack’s impact across the entire network.
Identifying Attack Source and Type, Watch what happens during a ddos attack
Identifying the source and type of DDoS attack is paramount for effective mitigation. The source might be a single botnet, a distributed network of compromised devices, or even a cloud-based attack infrastructure. Determining the source enables targeted mitigation strategies, such as blocking specific IP addresses or entire networks. Understanding the type of attack (e.g., volumetric, protocol, application-layer) guides the selection of appropriate mitigation techniques. A volumetric attack, such as a UDP flood, requires different mitigation strategies than an application-layer attack targeting a specific web application. For example, a volumetric attack might be mitigated by using scrubbing centers to filter out malicious traffic, while an application-layer attack might require implementing web application firewalls (WAFs) and rate limiting.
Key Data Points for DDoS Attack Investigation
Effective investigation necessitates collecting and analyzing several crucial data points. This includes timestamps of attack initiation and termination, source IP addresses and their geographical locations, attack vectors and protocols used, bandwidth consumption patterns, and the impact on network services and applications. This data allows security teams to reconstruct the attack timeline, identify the attacker’s tactics, techniques, and procedures (TTPs), and improve future defenses.
- Timestamps: Precise timing of attack onset and cessation, enabling accurate assessment of attack duration and impact.
- Source IP Addresses: Identification of originating IP addresses and their geographical location, pointing towards potential attacker locations.
- Attack Vectors and Protocols: Understanding the attack methods (e.g., SYN flood, UDP flood, HTTP flood) and protocols used, enabling targeted mitigation.
- Bandwidth Consumption: Monitoring network bandwidth usage to quantify the attack’s intensity and impact on network performance.
- Impact on Services: Assessing the attack’s effect on various network services and applications, helping to prioritize mitigation efforts.
Surviving a DDoS attack isn’t just about reacting; it’s about proactive defense. Understanding the mechanics of a DDoS, recognizing the symptoms, and implementing robust mitigation strategies are crucial for minimizing downtime and protecting your online presence. While a DDoS attack can feel like an insurmountable challenge, armed with the right knowledge and tools, you can significantly reduce its impact and bolster your defenses against future assaults. Remember, preparation is key in this ever-evolving digital battlefield.
 Invest Tekno Berita Teknologi Terbaru
Invest Tekno Berita Teknologi Terbaru