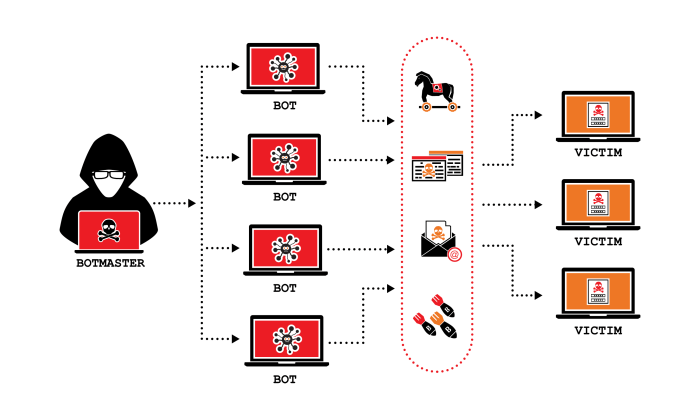
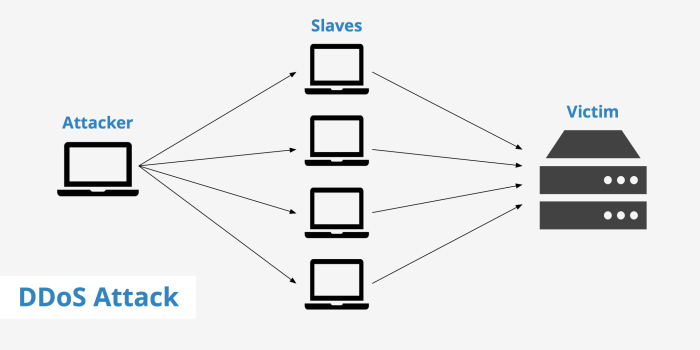
Ddos attackers using imessage with no relief in sight – iMessage DDoS Attacks: No Relief in Sight. That’s the chilling reality facing users and businesses alike. These attacks, leveraging the seemingly innocuous iMessage platform, are causing widespread disruption, from minor annoyances to crippling service outages. We’re diving deep into the mechanics of these attacks, exploring how attackers exploit vulnerabilities, the devastating consequences, and the frustratingly limited current mitigation strategies. Get ready to uncover the dark side of your favorite messaging app.
From individual users swamped with malicious messages to large organizations facing crippling service disruptions, the impact is far-reaching. We’ll examine real-world examples, delve into the technological challenges hindering effective prevention, and explore the legal and ethical quagmires surrounding this escalating threat. Ultimately, we’ll equip you with the knowledge and awareness needed to navigate this increasingly dangerous digital landscape.
Legal and Ethical Considerations: Ddos Attackers Using Imessage With No Relief In Sight
iMessage DDoS attacks, while seemingly a technical issue, carry significant legal and ethical weight. The consequences extend beyond simple network disruption, impacting individuals, businesses, and the broader digital landscape. Understanding these ramifications is crucial for both potential perpetrators and those tasked with preventing these attacks.
Legal Ramifications for Perpetrators
The legal repercussions for individuals involved in iMessage DDoS attacks vary depending on the scale and impact of the attack, the jurisdiction, and the specific laws violated. Generally, such actions can fall under existing cybercrime statutes, encompassing offenses like unauthorized access to computer systems, disruption of service, and potentially even extortion or harassment depending on the attacker’s intent and actions. Penalties can range from hefty fines to significant prison sentences. For instance, a large-scale attack crippling a critical infrastructure service would likely attract far more severe penalties than a smaller, localized attack targeting an individual. The involvement of multiple individuals further complicates the legal landscape, potentially leading to charges of conspiracy or aiding and abetting.
Ethical Implications of Malicious iMessage Use, Ddos attackers using imessage with no relief in sight
The ethical implications of using iMessage for malicious purposes are clear-cut: it’s wrong. Employing a communication platform designed for personal interaction to deliberately disrupt services and cause harm violates fundamental principles of digital responsibility and ethical conduct. This action disrupts the lives and businesses of innocent individuals, undermines trust in technology, and contributes to a less safe and secure online environment. The potential for significant harm, both financially and emotionally, underscores the profound ethical breach inherent in these attacks. The act of deliberately causing disruption is fundamentally unethical, regardless of the perceived justification or the perceived anonymity of the perpetrators.
Responsibilities of Technology Companies
Technology companies like Apple, which operates iMessage, bear a significant responsibility in mitigating the risk of DDoS attacks leveraging their platform. This responsibility extends to implementing robust security measures, investing in proactive threat detection and prevention systems, and collaborating with law enforcement to investigate and prosecute perpetrators. Failing to take appropriate measures can lead to legal liability, reputational damage, and a loss of user trust. This responsibility also includes providing users with clear guidance on how to identify and report potential attacks, and offering tools and resources to help protect themselves from such threats. The proactive development and deployment of advanced security protocols are paramount in reducing the vulnerability of their platform to such malicious exploitation.
Potential Legal Consequences Based on Attack Scale and Impact
| Attack Scale | Impact | Potential Legal Charges | Potential Penalties |
|---|---|---|---|
| Small-scale, targeting individuals | Minor inconvenience, limited service disruption | Harassment, cyberstalking, unauthorized access | Fines, community service, probation |
| Medium-scale, targeting businesses | Significant service disruption, financial losses | Disruption of service, computer fraud, conspiracy | Significant fines, imprisonment (several years), asset forfeiture |
| Large-scale, targeting critical infrastructure | Widespread service disruption, major financial losses, potential safety risks | Terrorism-related charges, sabotage, conspiracy, significant computer fraud charges | Extensive prison sentences (decades), massive fines, asset forfeiture |
| International, coordinated attacks | Global service disruption, significant economic damage | International cybercrime charges, conspiracy, racketeering | Extradition, lengthy prison sentences, international cooperation in prosecution and penalties |
User Awareness and Best Practices
iMessage, while convenient for personal communication, can unfortunately be a vector for Distributed Denial of Service (DDoS) attacks. Understanding how these attacks work and implementing proactive measures is crucial for protecting yourself and your devices. This section Artikels practical steps individuals can take to mitigate the risk of becoming a victim. Remember, prevention is always better than cure.
These attacks leverage the inherent limitations of iMessage’s design to overwhelm a target’s device or network. Understanding user vulnerabilities is key to building a robust defense strategy.
Identifying Suspicious Messages and Activities
Recognizing potentially malicious iMessages is the first line of defense. While attackers employ various techniques, some common indicators can help you identify suspicious activity. Being vigilant is your best weapon.
- Unexpected Messages from Unknown Senders: Messages from numbers or email addresses you don’t recognize should be treated with caution. Avoid opening links or attachments within these messages.
- Messages Containing Unusual Characters or Links: Look out for messages with a high density of unusual characters, especially those that look like gibberish or contain shortened, obfuscated URLs. These often mask malicious links.
- Messages Triggering Unexpected App Behavior: If receiving an iMessage causes your device to behave strangely (e.g., excessive battery drain, unexpected app crashes, or unusually high data usage), it could indicate malicious activity.
- Large Number of Messages from the Same Source: A sudden influx of messages from a single sender, especially if the content is repetitive or nonsensical, might signify a DDoS attempt.
- Messages with Excessive Media: A large number of images, videos, or audio files sent simultaneously could be part of a coordinated attack to overwhelm your device’s resources.
Practical Advice for Self-Protection
Implementing these best practices can significantly reduce your vulnerability to iMessage-based DDoS attacks. Proactive measures are essential for minimizing risk.
- Enable Two-Factor Authentication (2FA): This adds an extra layer of security to your Apple ID, making it harder for attackers to access your account and send messages from it.
- Regularly Update Your Software: Keep your iOS and iMessage software updated to benefit from the latest security patches and bug fixes.
- Be Cautious with Links and Attachments: Never open links or attachments from unknown senders or those you suspect to be malicious.
- Report Suspicious Activity: If you receive suspicious messages, report them to Apple immediately. This helps them identify and address potential threats.
- Consider Blocking Suspicious Senders: Use the built-in blocking feature in iMessage to prevent further contact from identified malicious senders.
- Monitor Your Device’s Performance: Pay attention to unusual behavior such as slowdowns, crashes, or excessive data usage, which could indicate a DDoS attack in progress.
Examples of User Behavior Contributing to Attacks
Certain user behaviors can inadvertently facilitate iMessage-based DDoS attacks. Understanding these vulnerabilities allows for better risk mitigation.
- Clicking on Unknown Links: Opening links from untrusted sources can expose your device to malware or lead to participation in an attack.
- Downloading Attachments from Unknown Senders: Downloading files from unknown sources can introduce malware onto your device, potentially making it part of a botnet used in DDoS attacks.
- Ignoring Security Updates: Failing to update your software leaves your device vulnerable to known exploits that attackers could leverage.
- Using Weak Passwords: Weak passwords make it easier for attackers to compromise your account and use it to launch attacks.
The relentless rise of iMessage DDoS attacks highlights a critical vulnerability in our increasingly interconnected world. While current mitigation strategies offer some protection, the evolving nature of these attacks demands a proactive and multi-faceted approach. Collaboration between Apple, security researchers, and users is crucial to develop more robust defenses and deter malicious actors. The fight against iMessage DDoS attacks is far from over, but understanding the threat is the first step towards building a more resilient and secure digital future. Stay informed, stay vigilant, and stay safe.
 Invest Tekno Berita Teknologi Terbaru
Invest Tekno Berita Teknologi Terbaru